Azure Blob
There are three parts to integrating Azure with Encord:
Authenticating your storage account for integration on the Azure platform.
Integrating Azure with the Encord platform. Strict client-only access can also be added in this step if necessary.
- Setting up Cross-Origin Resource Sharing (CORS) on Azure.
1. Authenticating Azure
You can authenticate Azure in two different ways:
Method 1: Generating an account-level SAS
In Azure, navigate to Storage Accounts under 'Azure services' and select the storage account you wish to integrate.

Next, click on Shared access signature in the 'Security + networking' section.
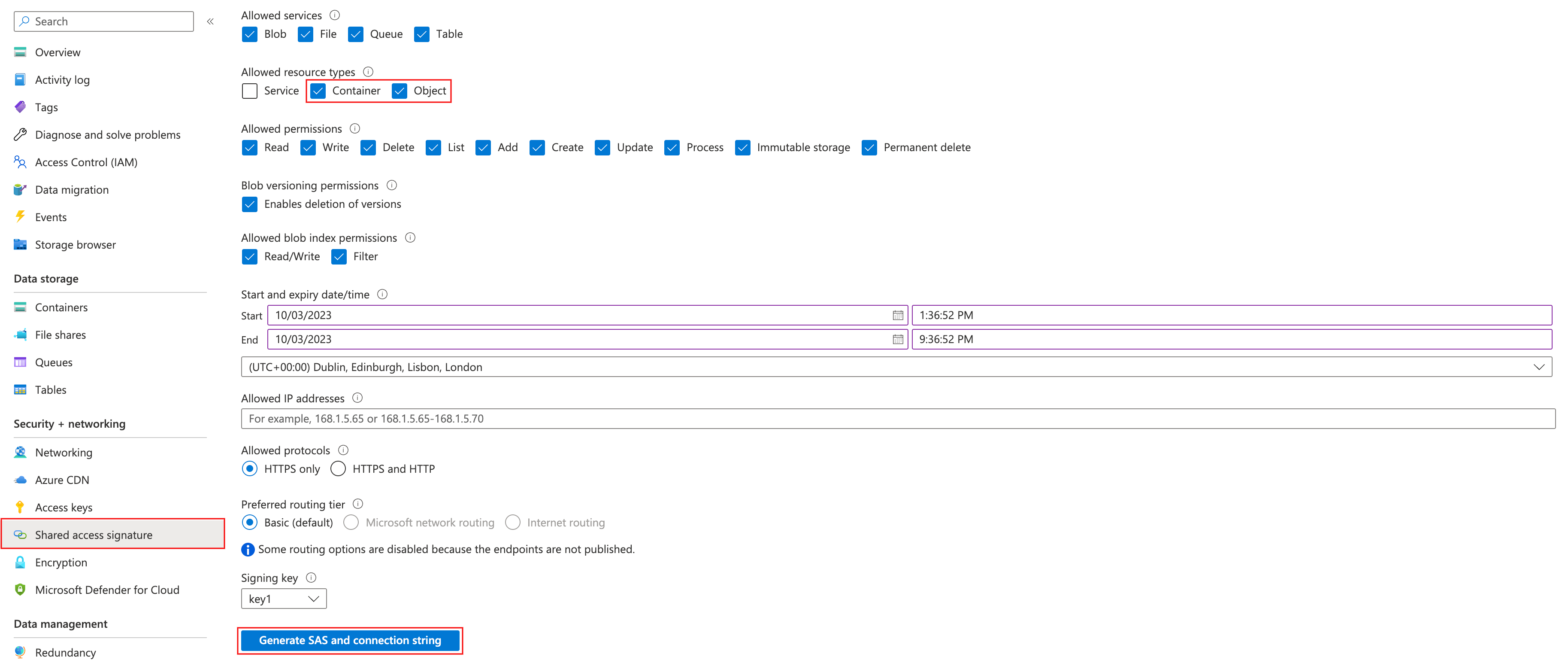
You'll need to check the 'Container' and 'Object' checkboxes under the 'Allowed resource types' heading. Please note the following permissions:
- Read (required)
- List (required)
- Write (recommended)
- Add (recommended)
- Create (recommended)
'Recommended' permissions are necessary to use some of our more advanced features such as 're-encoding' data, and 'optimized image groups'. Click Generate SAS and connection string when you are ready to generate your account-level SAS token.
Your SAS token will have a start and end date that can be adjusted, and it will only be valid for the specified time period. Expired tokens will have to be updated.
Now that you have generated your account-level SAS token, move on to the 'Creating the integration' section.
Method 2: Using a service principal
Using a service principal to authenticate you require you to:
Adding the cord-integrator app to Azure tenant
There are three different ways to add the cord-integrator app to Azure tenant:
Via a browser.
Via Azure powershell.
By granting storage account and container permissions to cord-integrator.
You need to have admin privileges for your Azure account to authenticate via a service principal.
Adding the cord-integrator app via a browser
You can add the cord-integrator application by following this link. If logged in to the Encord platform, you will be redirected to the 'Azure integration' screen after the application was successfully added.
Adding the cord-integrator app via Azure Powershell
New-AzADServicePrincipal -ApplicationId ab859d51-5577-4d6d-9b87-544df597f38a
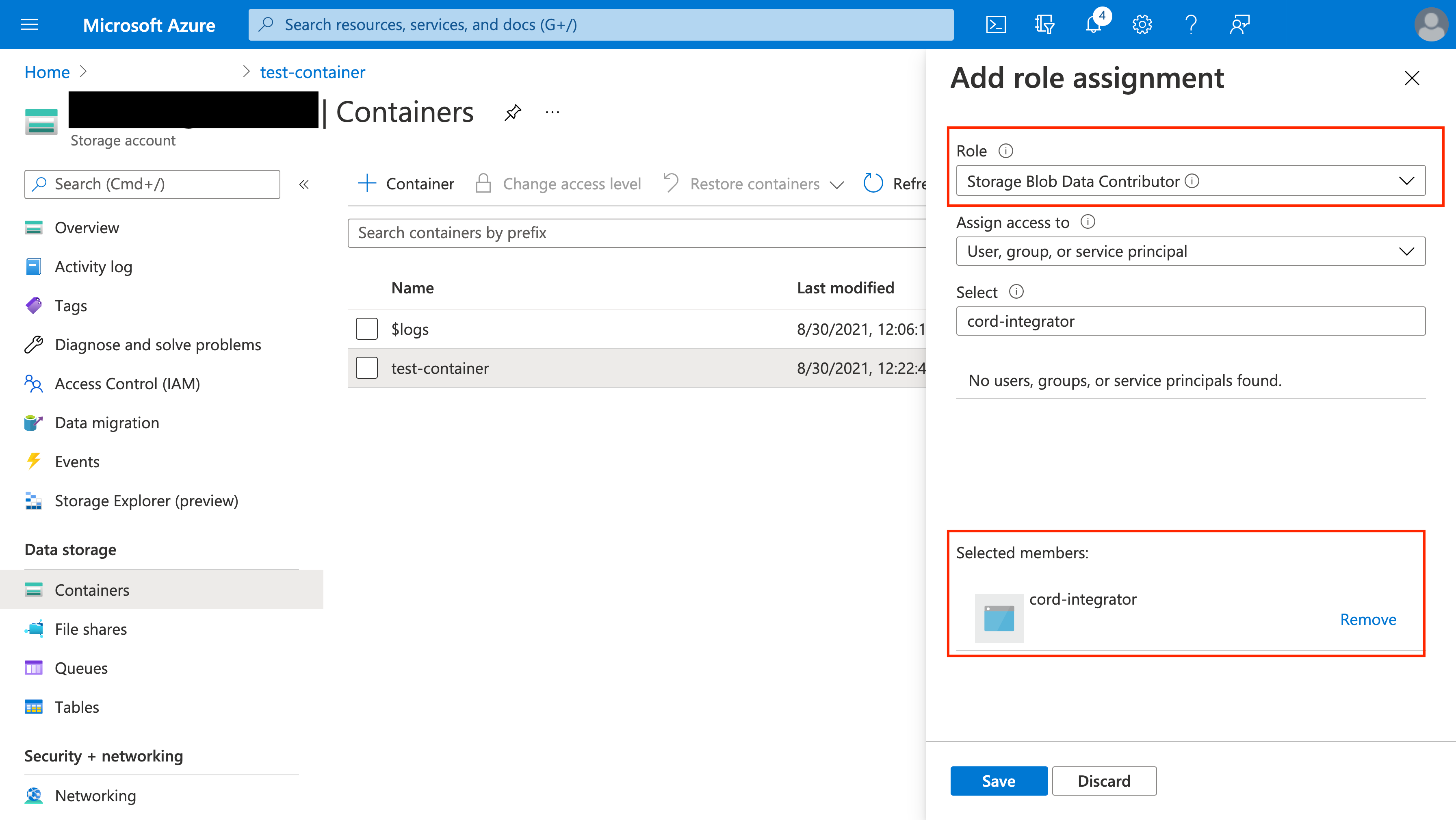
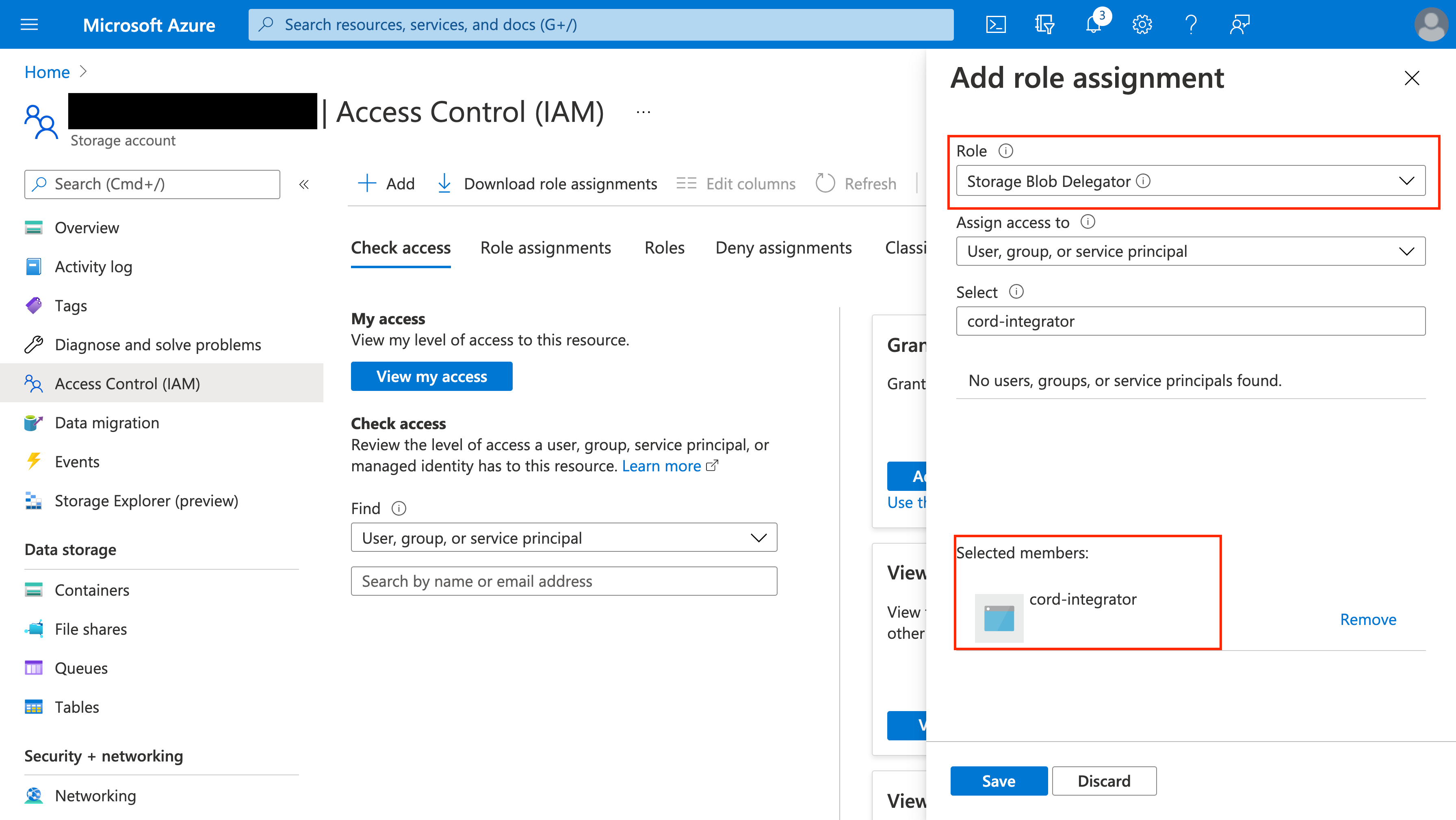
Granting storage account and container permissions to cord-integrator
The cord-integrator must be granted two types of permissions in order to function:
- The Storage Blob Data Contributor role at the container level
- The Storage Blob Delegator role at the storage account level
Find your Azure tenant ID
You can find the Azure Tenant ID in the Active Directory overview of your Azure project.
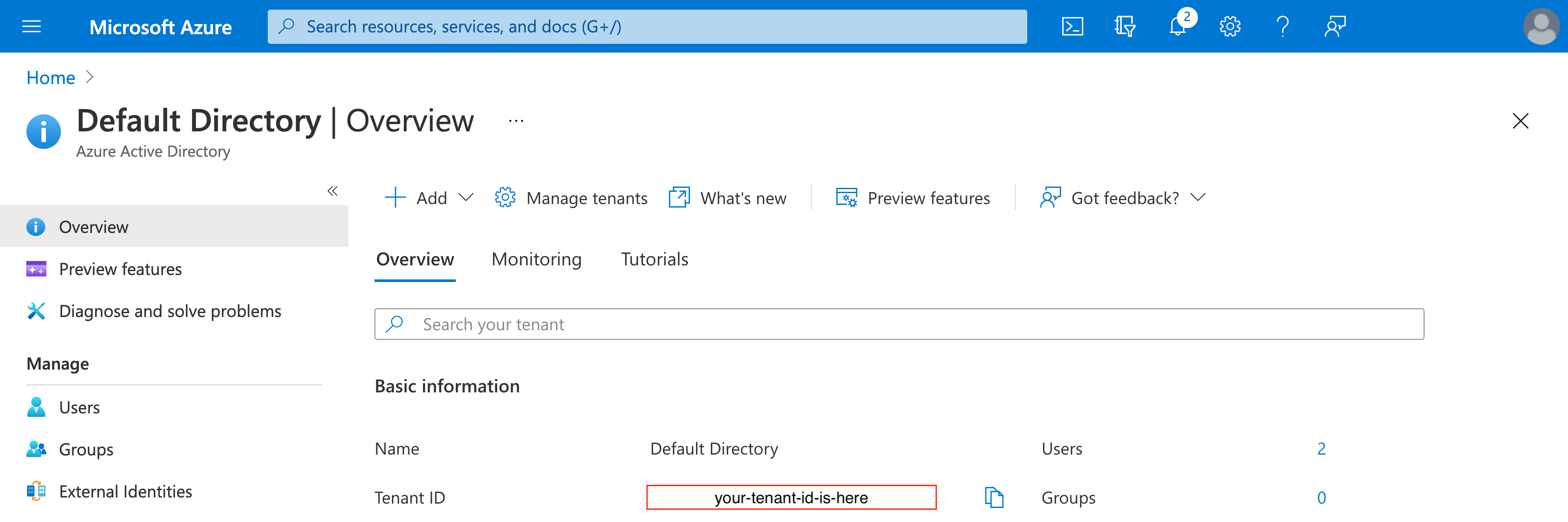
After you have added the cord-integrator app, granted it storage account and container permissions, as well as located your Azure tenant ID you are ready to create the integration.
2. Creating the integration
On Encord, navigate to your Settings from the dropdown on the top right.
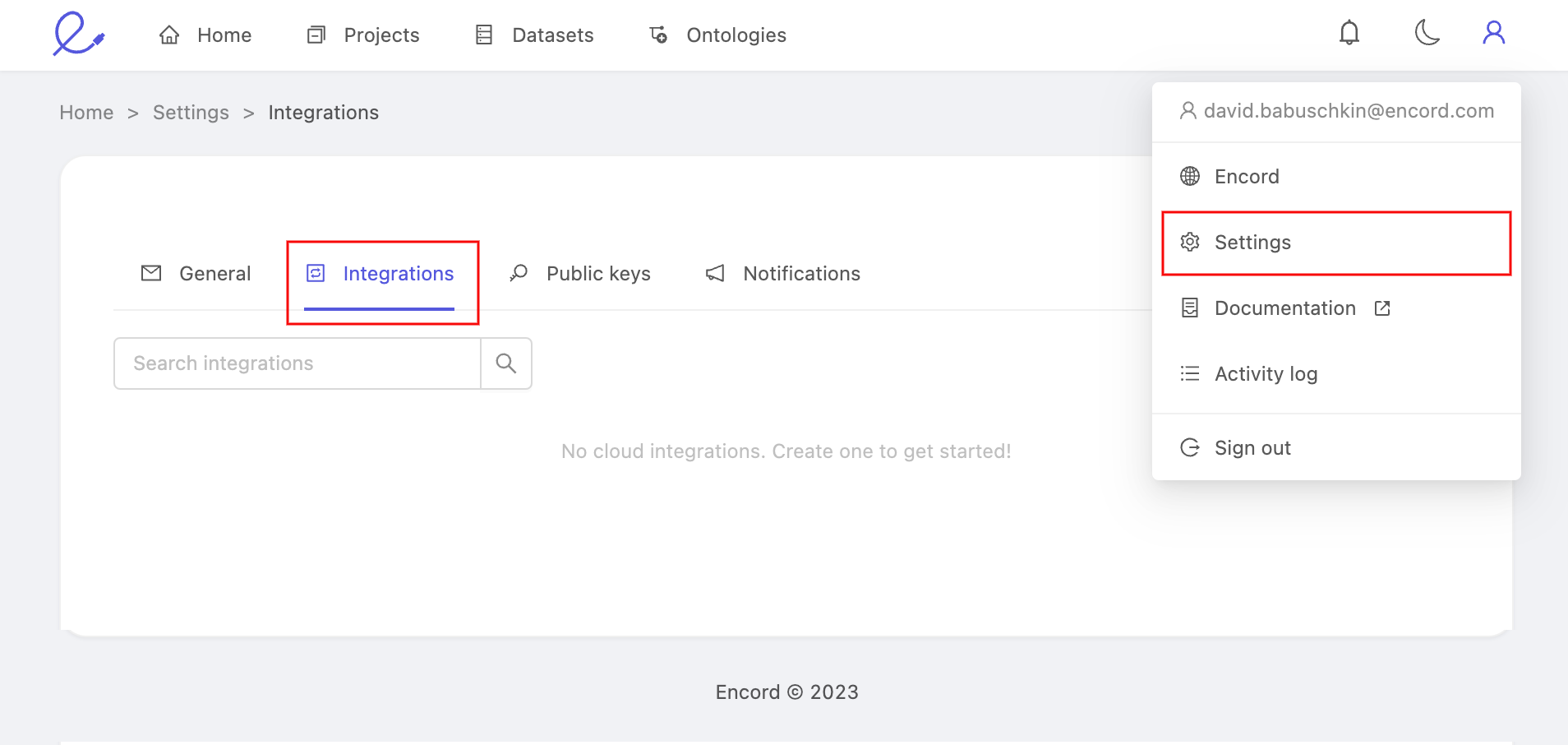
Open the 'Integrations' tab and click the Create integration button.
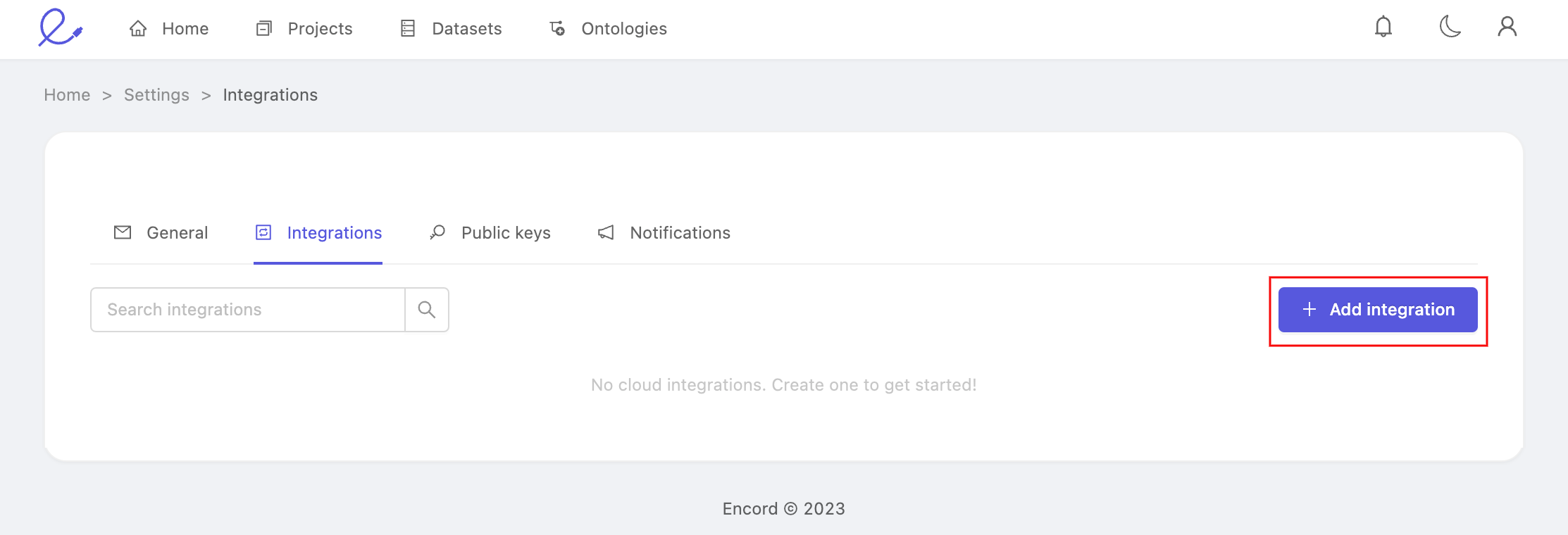
Navigate to the 'Azure tab' and select your preferred method of authentication by clicking on either Authenticate via a service principal, or Authenticate via an account-level shared access signature.
Optionally check the box to enable Strict client-only access, server-side media features will not be available if you would like Encord to sign URLs, but refrain from downloading any media files onto Encord servers. Read more about this feature here.
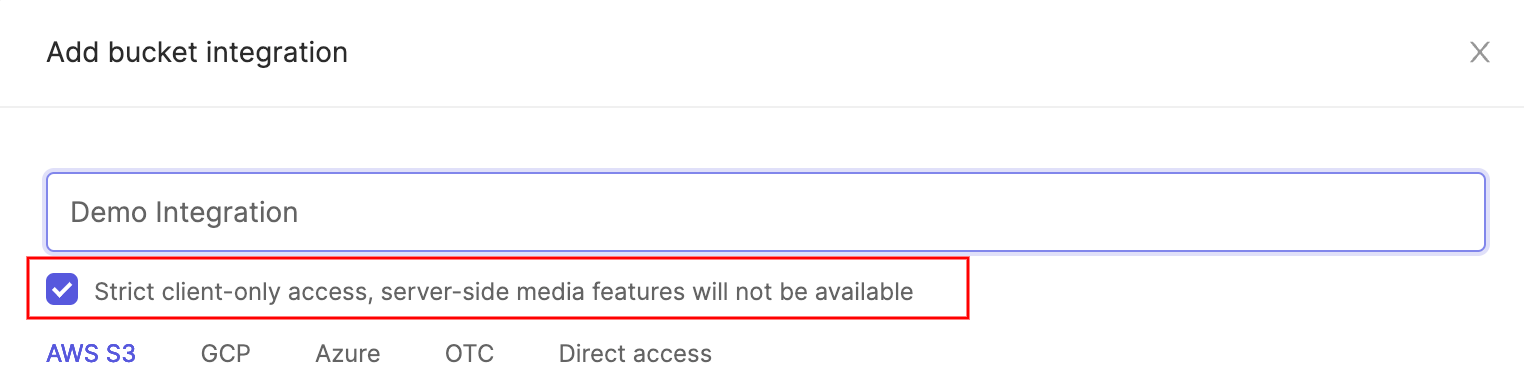
Authenticate via account-level SAS token
To authenticate using an account-level SAS token click on Authenticate via an account-level shared access signature.
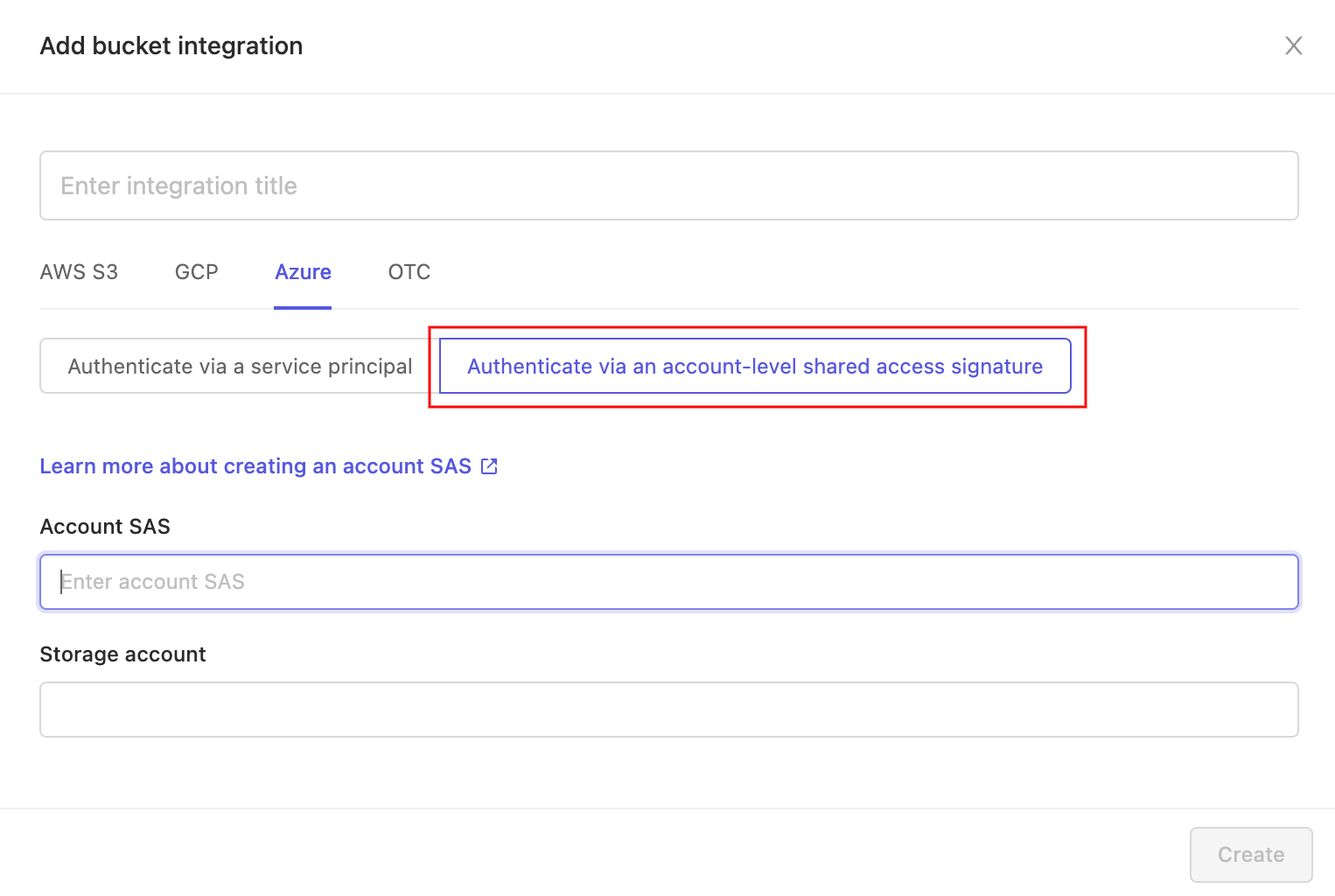
Choose a name for the integration. Then enter the account-level SAS token you generated in Azure, as well as the name of the storage account you with to integrate into the specified fields. The Create button - which becomes available as soon as all fields have been filled in - completes the integration. The integration will now be listed in the 'Integrations' tab of your Settings.
Authenticate via a service principal
To authenticate using an account-level SAS token click on Authenticate via a service principal.
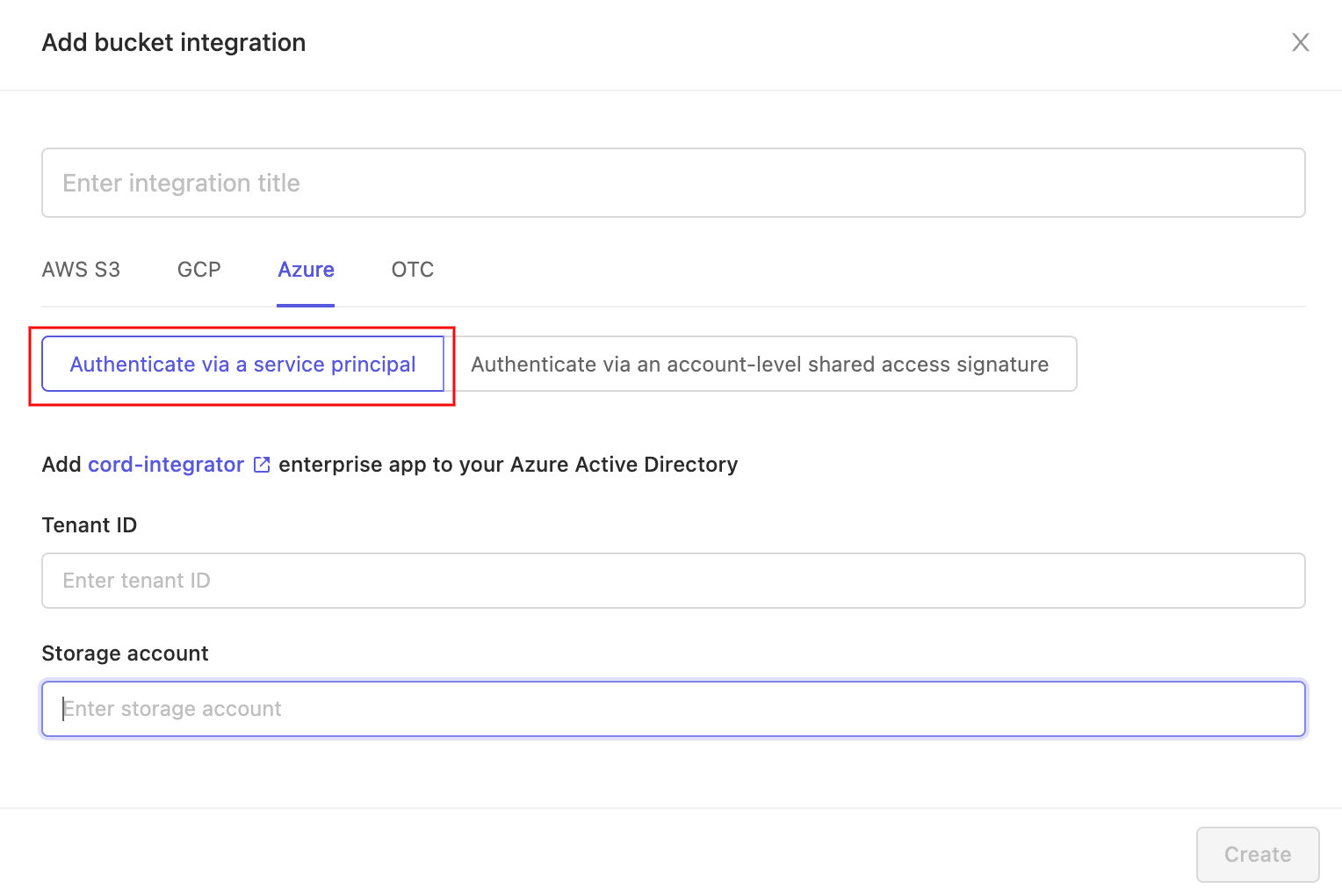
Choose a name for the integration. Then, enter your Azure tenant ID, and the name of the storage account you with to integrate into the specified fields. The Create button - which becomes available as soon as all fields have been filled in - completes the integration. The integration will now be listed in the 'Integrations' tab of your Settings.
3. Creating a CORS configuration in Azure
A CORS configuration needs to be applied to the Azure storage account you wish to integrate with Encord. This will enable your users' browsers to request resources from the specified service account.
Navigate to the 'Resource Sharing (CORS) section under 'Settings' of your storage account.
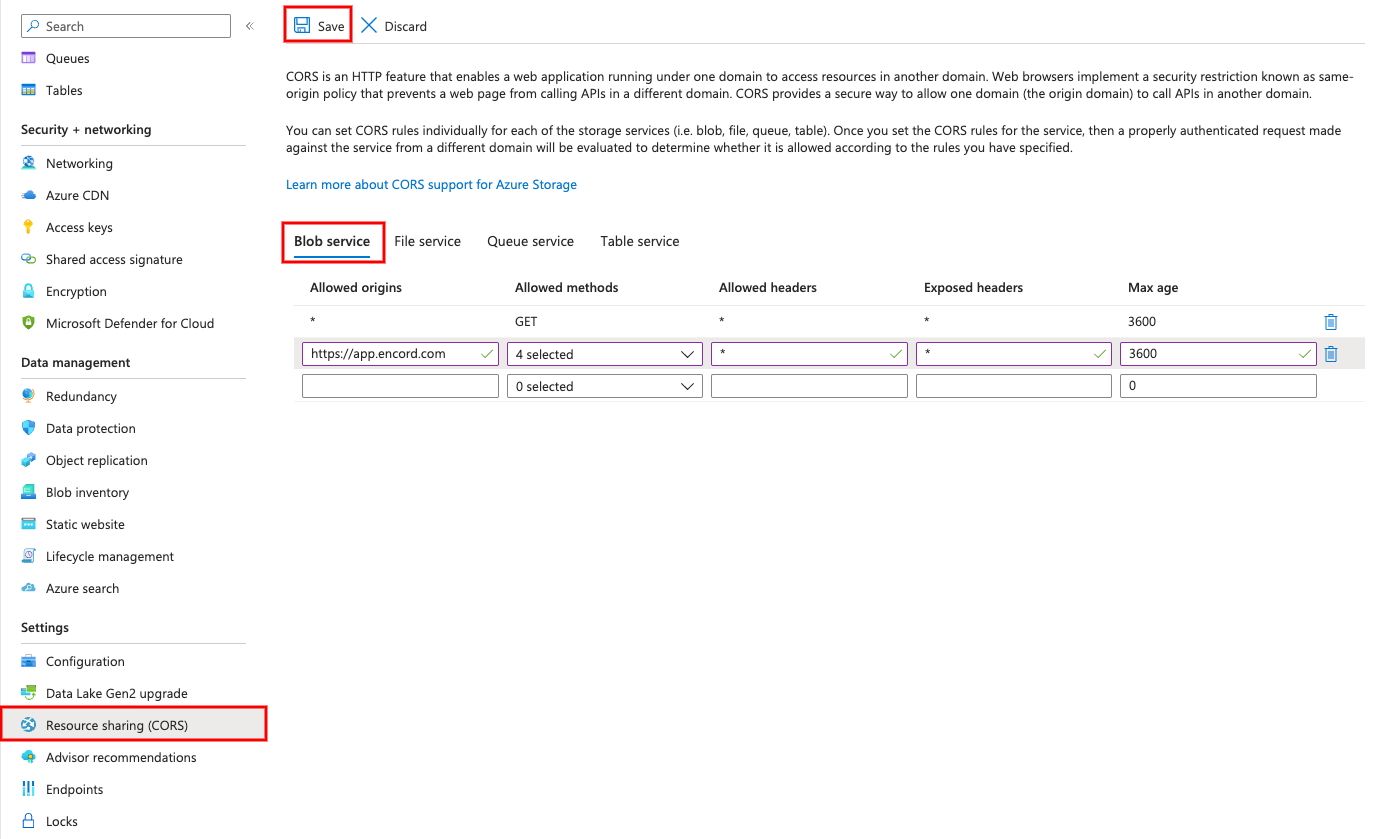
Input the following values in the 'Blob service' tab of Resource Sharing (CORS) page:
| Allowed origins | Allowed methods | Allowed headers | Exposed headers | Max age |
|---|---|---|---|---|
| https://app.encord.com | GET, POST, OPTIONS, PUT | * | * | 3600 |
In the example above, preflight requests are valid for 1 hour. Use the 'Max Age' variable to adjust the number of seconds the browser is allowed to make requests before it must repeat the preflight request.
Click Save to save the CORS configuration.
4. Testing your integration
To test that Encord can sync with your Azure storage, click the ![]() icon where you integration is listed.
icon where you integration is listed.
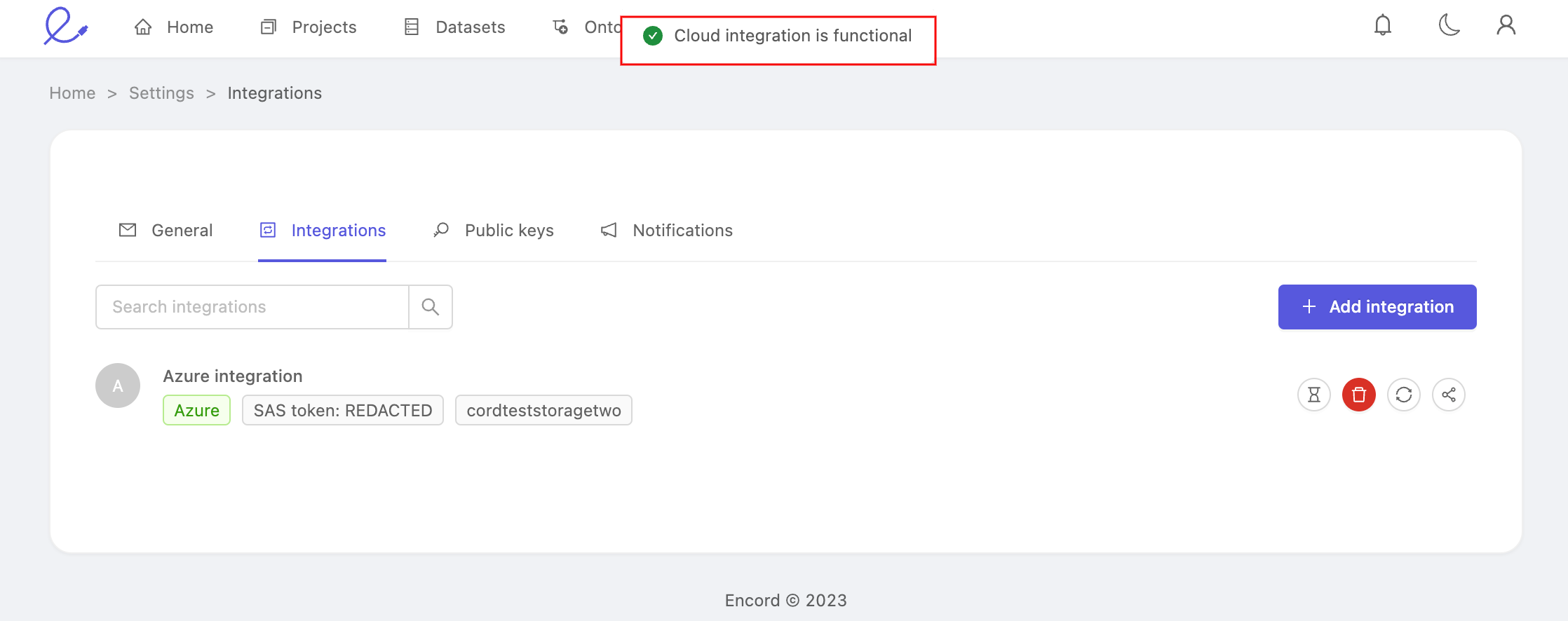
If the sync is successful, you will see a message saying that the integration is functional.
5. Updating expired account-level SAS tokens
This section is only applicable if you used an account-level shared access token to authenticate.
Shared access tokens expire and have to be updated in order to continue providing Encord with access to your Azure storage. To do so, simply click the  icon on your Azure integration, as seen below.
icon on your Azure integration, as seen below.
Generate a new account-level SAS token and paste it into the pop-up that appears.
6. Creating a dataset with Azure data
Please navigate to the private cloud integration section for guidance on how to create a dataset with data stored in Azure.